Differentiate private key and public key cryptography with at least 3 points each images are ready. Differentiate private key and public key cryptography with at least 3 points each are a topic that is being searched for and liked by netizens now. You can Download the Differentiate private key and public key cryptography with at least 3 points each files here. Get all free images.
If you’re looking for differentiate private key and public key cryptography with at least 3 points each pictures information connected with to the differentiate private key and public key cryptography with at least 3 points each keyword, you have visit the right blog. Our site frequently provides you with hints for seeking the maximum quality video and image content, please kindly hunt and find more enlightening video content and images that match your interests.
Differentiate Private Key And Public Key Cryptography With At Least 3 Points Each.

 Chapter 3 Public Key Cryptography And Message Authentication Ppt Download From slideplayer.com
Chapter 3 Public Key Cryptography And Message Authentication Ppt Download From slideplayer.com

 Source: sectigostore.com
Source: sectigostore.com
 Source: condor.depaul.edu
Source: condor.depaul.edu
 Source: preveil.com
Source: preveil.com
 Source: slideplayer.com
Source: slideplayer.com
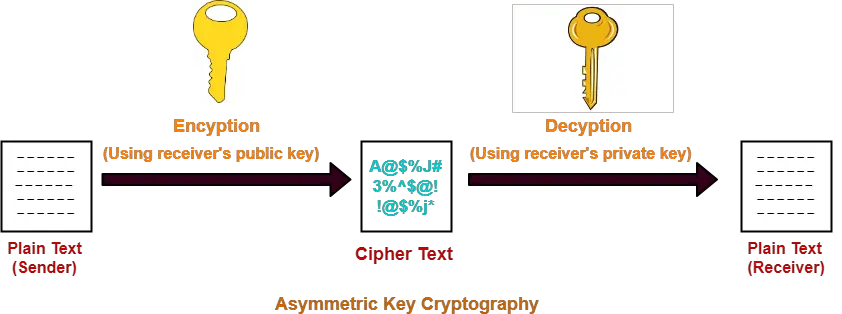 Source: gatevidyalay.com
Source: gatevidyalay.com
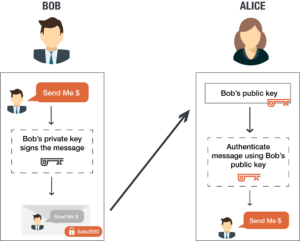 Source: preveil.com
Source: preveil.com
 Source: usna.edu
Source: usna.edu
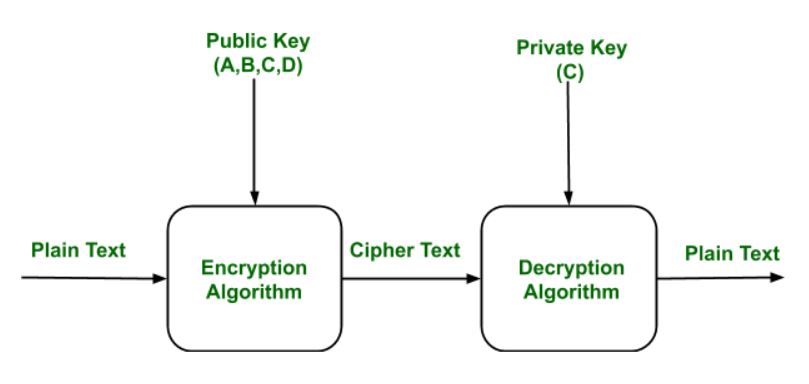 Source: geeksforgeeks.org
Source: geeksforgeeks.org
 Source: sciencedirect.com
Source: sciencedirect.com
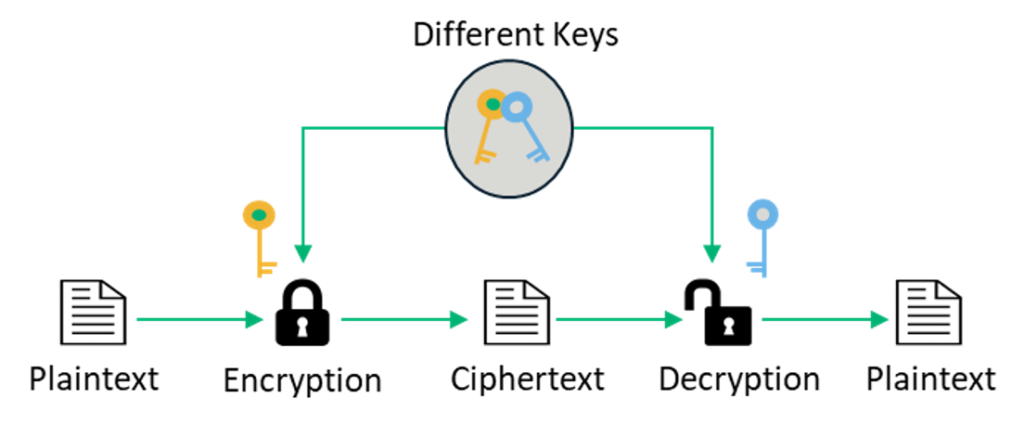 Source: sectigostore.com
Source: sectigostore.com
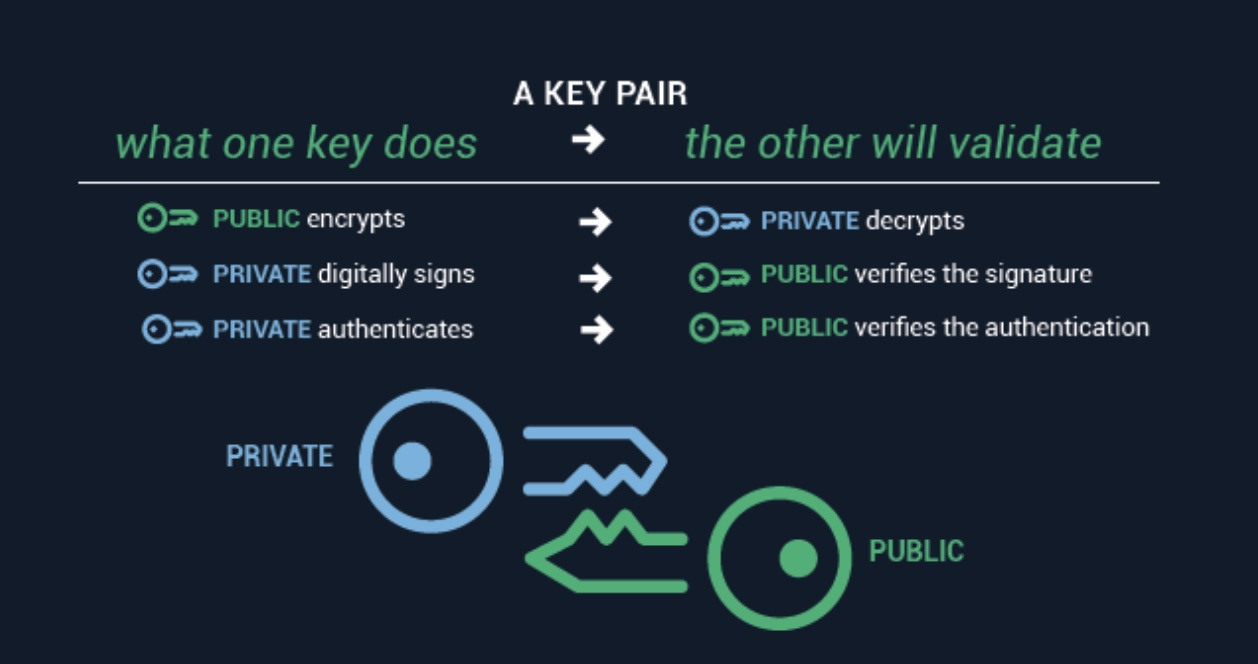 Source: sectigo.com
Source: sectigo.com

This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title differentiate private key and public key cryptography with at least 3 points each by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.